Writing up a quick run-through of OllyDbg for a personal reference and information capturing. I’m sitting a Malware Analysis unit for University and had some trouble with navigating OllyDbg.
Environment #
I’m running VMWare Workstation with a Win10 machine equiped with some handy malware analysis tools. There’s a rollback snapshot stored within VMWare so I can recover as needed.
Reverse Engineer with IDA #
Let’s try work through a simple program without reviewing any original source code.
We’ll pop open our executable in IDA and hunt for our main function:
From here we can see that there’s some kind of control flow that, after an evaluation, prints either “You Won!” or “You Lost.”.
Looking at the diagram, there’s a cmp flag which indicates an if statement occurs, controlling the remaining flow:
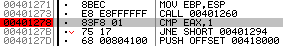
This works out as: Compare the value in the eax register to 1. If equal, print “You Won!”, else print “You Lost.”.
Further to this, we can confirm that the default behaviour of the program is to lose. Using Ida, we’ll investigate the call function directly above the cmp function:
This simple function pushes the value “2” onto the EAX register, causing the comparison to evalutate to False.
Exploit with OllyDbg #
Now that we’ve analysed the behaviour with IDA, we’ll open the executable in OllyDbg to change the EAX value at run time.

Using the keyboard shortcut Alt+M to open the memory map viewer, we’ll locate our program entry point for further analysis:
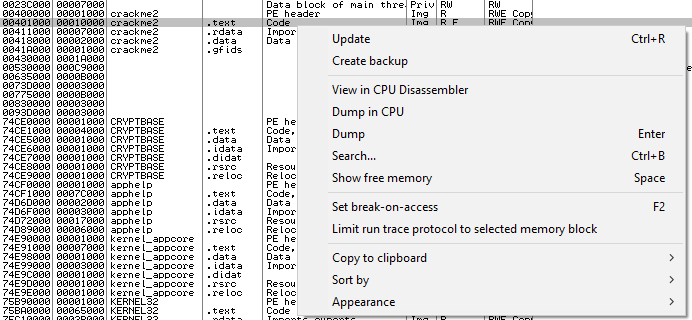
By selecting view in dissassembler on the entry point, we are taken directly to our main function entry.
From here, we’ll locate the memory address for the cmp instruction, and set a breakpoint with the F2 keyboard shortcut:

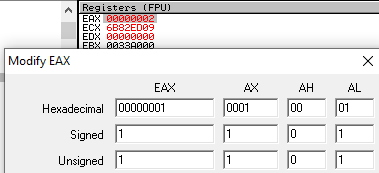
Now we’ll run the program. Once we hit the breakpoint, we’ll edit the EAX register in the right-hand window, and set it to the value in the cmp function (“1”):

Now we’ll continue running the application and receive the “You Won!” message
